Hi everyone, these days are the hardest days we have been experiencing, so many attacks, some security breaches we have been found, then we have to act accordingly, I want to share with you the policies you have to deploy and the highlight you have to take under your consideration for implementing.
Let’s begin because we have a lot of work!
Due to CryptoLocker, we need to ensure that we block the possibility to run executable files on Temp and AppData folders.
We can disallow it to any user and prevent to run execution file or 7z, RAR, Wz, files on App data by creating a new “Addition Rules” policy in Group Policy,
Please follow the GPO you should apply:
** Make sure you have no problem with Office installation.
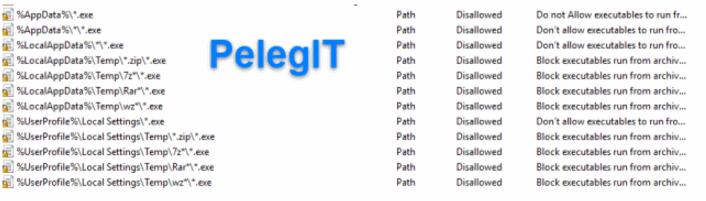
Policies you might apply:
Path: %AppData%\*.exe
Security Level: Disallowed
Description: Don’t allow executables to run from %AppData%.
Block CryptoLocker executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*.exe
Security Level: Disallowed
Description: Don’t allow executables to run from %AppData%.
Block Zbot executable in %AppData%
Path: %AppData%\*\*.exe
Security Level: Disallowed
Description: Don’t allow executables to run from immediate subfolders of %AppData%.
Block Zbot executable in %LocalAppData%
Path if using Windows XP: %UserProfile%\Local Settings\*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\*\*.exe
Security Level: Disallowed
Description: Don’t allow executables to run from immediate subfolders of %AppData%.
Block executables run from archive attachments opened with WinRAR:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\Rar*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\Rar*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinRAR.
Block executables run from archive attachments opened with 7zip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\7z*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\7z*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with 7zip.
Block executables run from archive attachments opened with WinZip:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\wz*\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\wz*\*.exe
Security Level: Disallowed
Description: Block executables run from archive attachments opened with WinZip.
Block executables run from archive attachments opened using Windows built-in Zip support:
Path if using Windows XP: %UserProfile%\Local Settings\Temp\*.zip\*.exe
Path if using Windows Vista/7/8: %LocalAppData%\Temp\*.zip\*.exe
Security Level: Disallowed
Download and install Office 2016 ADMX file into your GPO, download it from here:
https://www.microsoft.com/en-us/download/details.aspx?id=49030
How to add AMDX to GPO:
https://pelegit.co.il/how-to-add-admx-or-adm-file-to-group-policy/
Block Office Macro from running:
Microsoft Excel 2013/2016/ Excel Options/Security/Trust Center:
Add Office 2016 ADMX file and apply the following Policy:
Block macros from running in Office files from the Internet – Enabled
VBA Macro Notification Settings – Enabled
Microsoft Excel 2013/2016/ Excel Options/Security/Trust Center/Protected View:
Do not open files from the Internet zone in Protected View – Disabled
Do not open files in unsafe locations in Protected View – Disabled
Set document behavior if file validation fails – Enabled
Turn off Protected View for attachments opened from Outlook – Disabled
Microsoft Outlook 2013/2016/ Security/Trust Center:
Security setting for macros – Enabled
Security Level Always warn
Microsoft Word 2013/Word Options/Security/Trust Center
Block macros from running in Office files from the Internet – Enabled
VBA Macro Notification Settings – Enabled [Disable all with notification]
Microsoft Word 2013/2016/ Word Options/Security/Trust Center/Protected View
Do not open files from the Internet zone in Protected View – Disabled
Do not open files in unsafe locations in Protected View – Disabled
Turn off Protected View for attachments opened from Outlook –Disabled
According to this discussion, you can see that it is recommended to deploy ShowOLEPackageObj:
http://www.edugeek.net/forums/how-do-you-do/159149-cryptolocker-prevention-5.html
Deploy the registry key ShowOLEPackageObj, for your version(s) of Office, to silently disable OLE Package function in Outlook:
Hive HKEY_CURRENT_USER
Key path:
Software\Policies\Microsoft\office\15.0\outlook\security
Value name: ShowOLEPackageObj
Value type: REG_DWORD
Value data: 0x0 (0)
Apply once and do not reapply: Yes
Additionally, I would apply this policy:
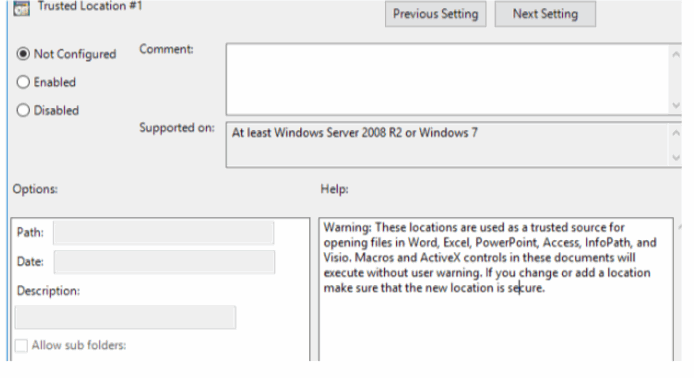
Trusted location:
Microsoft Office 2013/2016/Security Settings/Trusted Center/trusted Location
Warning: These locations are used as a trusted source for opening files in Word, Excel, PowerPoint, Access, InfoPath, and Visio. Macros and ActiveX controls in these documents will execute without user warning. If you change or add a location make sure that the new location is secure.
How to apply UAC:
Remove Local Administrator thought Active Directory:
Consider change Local Administrator name to different Name, it is possible to change it broadly entire domain:
https://technet.microsoft.com/en-us/library/cc747484(v=ws.10).aspx
In a bottom line.
You have all instructions, all scripts you need for protecting your organization just, take responsibility for your IT infrastructure and initiate internal projects.
I would check any policy into lab environment for some day before deploying it to the production environment.
I can’t guarantee it will avoid any ransom or any attack, as you’re experiencing right now what goes on and seeing that there are many many holes we must seal, easier and in safety, we are doing the best to complete our job as IT guys.