Hi all,
This week I had an interesting task to complete, too much time invested on it and it was very important for me to share that with you, it is a good solution for organizations that have Office 365 and or applications in Windows Azure
Just a couple of words about Azure AD Join, one of amazing advantage we have in Windows 10 is the possibility to register a device into Windows Azure per device, have several ‘hopes‘ to pass and eventually we have to insert email address and password and that all we SSOing to Office 365 (if there is any application also there mostly credential is required).
For real guys, your PC will register on Azure AD and then we will be to perform login automatically to office 365 without inserting credential. No doubt, definitely amazing feature, no ADSF is required or any other service, the requirements will show you later.
Using this configuration we are allowing to users performing SSO, regardless user’s device is registered in Office 365 or not. once the “AzureAdJoined” value is set to YES it means that the configuration configured properly
The SSO knows to allow you SSO with
What you have to do\ How to configure it?
Go to your Azure environment and navigate to your main AD and go to “Configure”
Scroll down to “devices“, and enable the following settings:
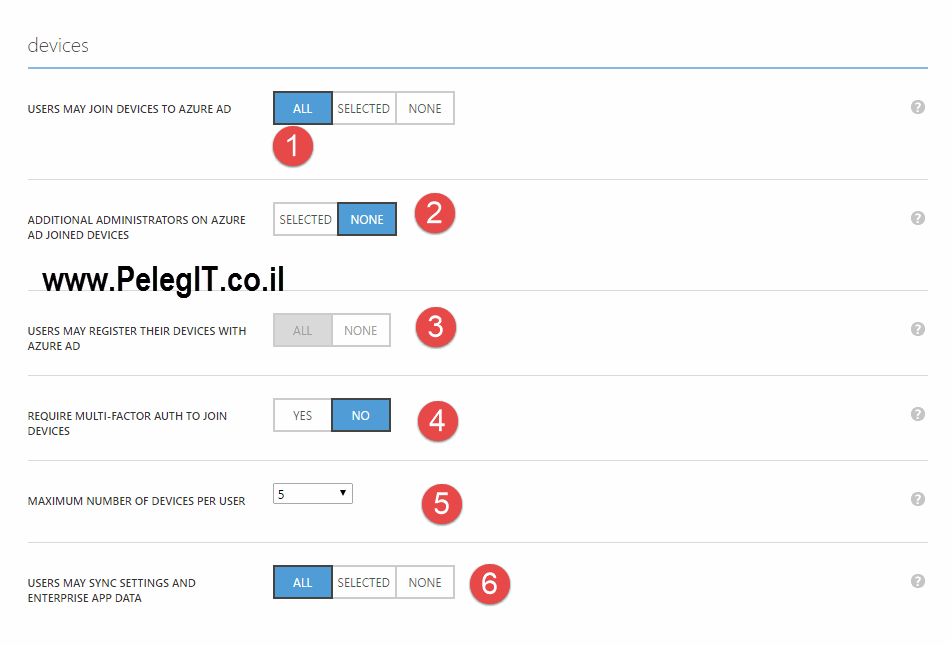
Just let you know, furthermore, you can set a maximum number of devices per user and other settings.
for Management level, that’s it! now we just have to register machine by clicking on this button: “Join Azure AD”

Of course, we aren’t going to do that manually per a computer, so there is GPO that we should use on GPO for enabling it (make sure you have Windows 10 ADMX files If you do not have it, you can check out this here Link)
Create a new GPO and allows this GPO to computers you want to join Azure AD automatically:
Computer Configuration/Policies/Administrative Templates/Windows Components/Workplace Join
Guess what?
If you run in CMD windows > Run > Cmd > “dsregcmd.exe /status” you may get “AzureadJoined” value as “No“, it takes us a while to realize that I have to configure Service Connection Point (SCP) in order to make use of AzureADJoin. it means that the SCP holds the discovery information about my AD Azure tenant, so my clients can’t know who’s our tenant, so basically the SCP located at:
Open the ADSI.EDIT and find it out under CN=Configuration,DC=example,DC=com
CN=62a0ff2e-97b9-4513-943f-0d221bd30080,CN=Device Registration Configuration,CN=Services,[Your Configuration Naming Context]
If it doesn’t exist over there, go to your Dirsync server and open import Azure PowerShell model and run the following commands (AD module is required as well):
Import-Module -Name "C:\Program Files\Microsoft Azure Active Directory Connect\AdPrep\AdSyncPrep.psm1"; $aadAdminCred = Get-Credential; Initialize-ADSyncDomainJoinedComputerSync –AdConnectorAccount [connector account name] -AzureADCredentials $aadAdminCred;
About “Connector account name” value you to have open the Synchronization Service and check what is the Azure Connector.
Once it is done, go back to your PC and restart your computer, Run through CMD “dsregcmd.exe \status” again”, and now AzureadJoined supposed to be YES.
Nowadays only Internet Explorer and Edge are supported for SSO.
For any other troubleshooting, you can run from the client “Dsregcmd.exe \debug” and then gather a useful information and status what’s going on, BTW, You can see how many “Devices” has to the users, in Azure go to users and then select a user, then select “Device” and you will see any machine that belongs to that particular user.
Many thanks to Tomer Ktzir from U-BTech.