How to Configure Credential Guard Windows 10
I would like to show you how to configure credential guard in Windows 10, the Credential guard is one of the major security features that come with Windows 10, Credential Guard protects us against hacking and obtaining of credential in Windows, undoubtedly, you have heart about Mimiktaz tool, which can obtains your password as clear-text simply by perform pass-the-hash, pass-the-ticket or build Golden tickets.
You know what, don’t say I am not a friend, let’s demonstrate you a couple of actions with Mimiktaz.
Download the tool from Google, it is available for anyone.
– Make sure AV is not blocking it.
mimikatz:
https://github.com/gentilkiwi/mimikatz/releases
while you’re opening the mimikatz, copy the following commands in notepad because I will use them again later, and run the following commands:
– Run Mimikatz as Administrator.
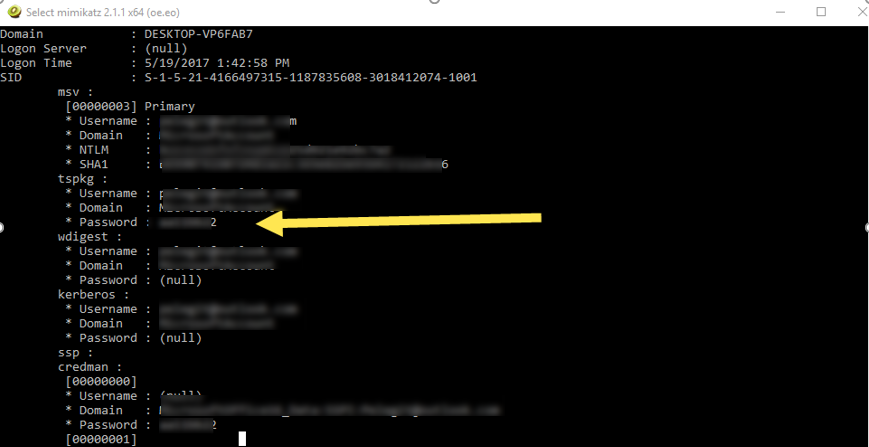
Run the following commands:
mimikatz # privilege::debug mimikatz # sekurlsa::logonPasswords full
Look at that, just couple of simple actions and you are able to retrieve Local and Administrator password, how much time does hacker take to run it on your computer? less than 5 sec, that’s what he needs.
The reason you just see the 2 number is because I have blurred it on purpose – it is my personal Password 💡
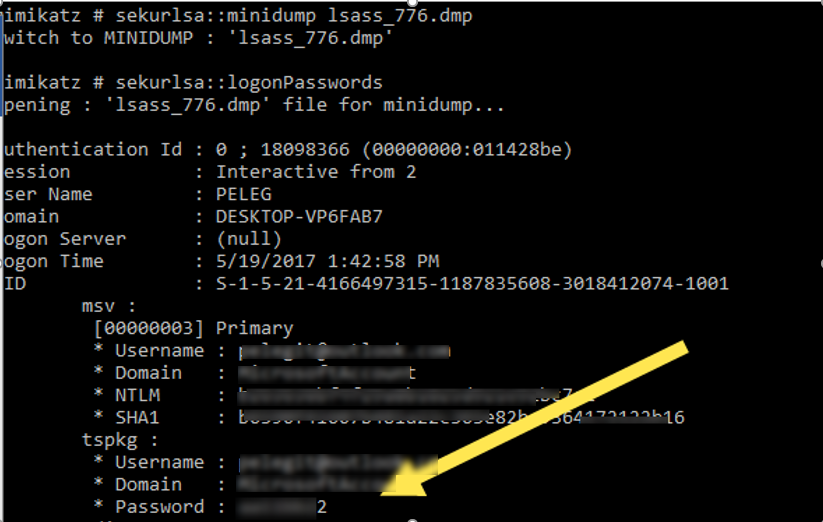
On top of that you can get user’s password from Windows Memory Dump:
The purpose is to take a memory dump of LSASS.exe process and then Run minidump with mimikatz, it can be generated by using this script, we can see the memory dump on PowerShell,
Link:
https://raw.githubusercontent.com/mattifestation/PowerSploit/master/Exfiltration/Out-Minidump.ps1
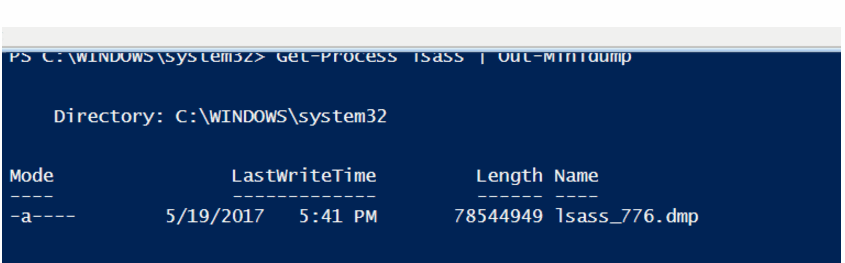
Then, using Mimikatz, run the following commands:
If you are getting error ERROR kuhl_m_sekurlsa_acquireLSA ; Handle on memory (0x00000002)
The minidump file is not found, change directory with CD
sekurlsa::minidump lsass_776.dmp sekurlsa::logonPasswords
Unbelievable so simple, here are the answers
Do not get confuse guys, it is working wonderful, they definitely put Microsoft on the spot.
So, how can we prevent it to occurs in your organization?
Break the Ice and begin with Windows 10 project in your company, these settings valid only on Windows 10 & Windows Server 2016, Scratch deployment is suggested because there are some prerequisites you might do.
Please follow the steps and the requirements:
- Make sure you have enabled UEFI mode, Secure boot and (TPM recommended but not required) under your BIOS- regarding TPM if you have it enable it because the credential guard can be protected by TPM:
https://social.technet.microsoft.com/Forums/windows/en-US/5d0ddfeb-daeb-4487-a552-db5dd8f2319a/credential-guard-with-no-tpm?forum=win10itprosecurity - Your Windows 10 machines must be Enterprise or Education edition.
- Ensure you have enabled VSM (Virtual secure mode) which is Hyper-V container that isolates the Lsass.exe from running normally on Windows 10 and running it on hyper -v hypervisor,
Enable “Hyper-V Platform” on your machines:
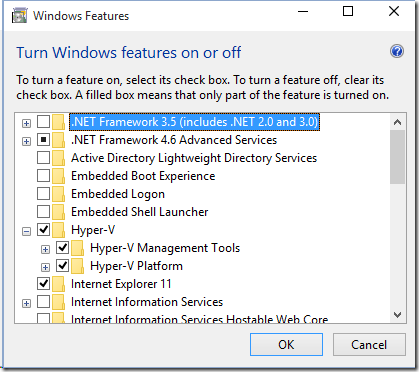
•Enable VSM by Group Policy:
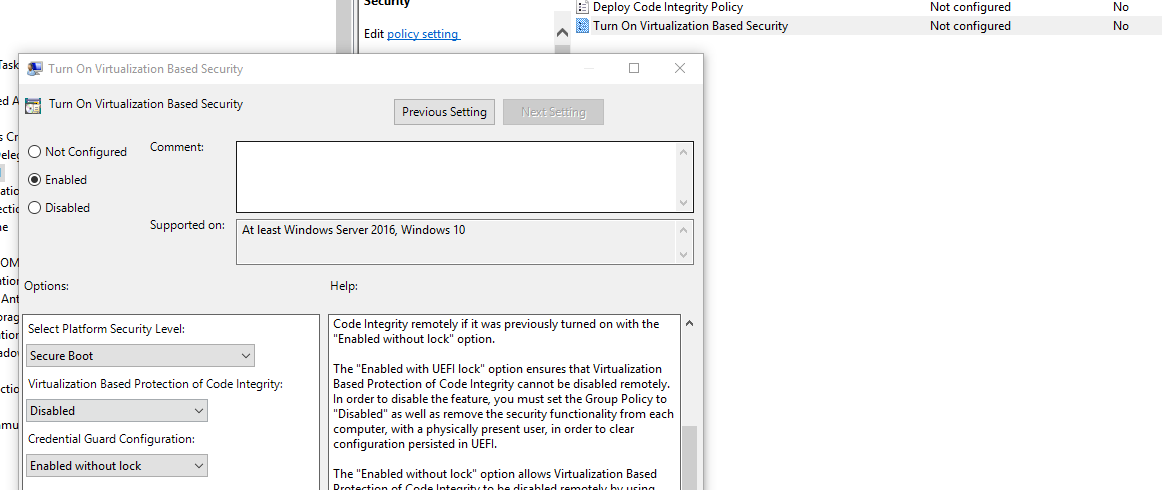
Computer Configuration\Administrative Templates\System\Device Guard
Select the “Turn on Virtualization Based Security” and do exactly like this:
In order to start VSM you can use this command- then restart the computer.
bcdedit /set vsmlaunchtype auto
- If your BIOS mode is legacy, it won’t work, you must use on UEFI mode, using UEFI the disk converted to GPT.
Nowadays, if you use in Windows 10 1703 you can convert your disk using “mbr2gpt disk conversion tool” which is available on 1703 [Creator update].
- If you have SCCM, make use of this tool, it will be faster.
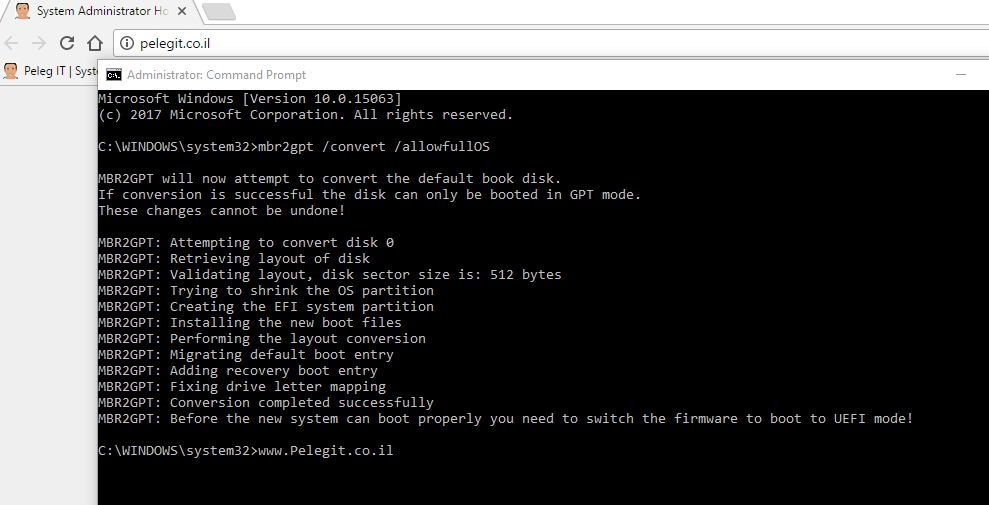
Let’s convert my computer from MBR to GPT using mbr2gpt tool:
Open CMD as Administrator privilege:
mbr2gpt /convert /allowfullOS
Then restart your computer and change BIOS mode to UEFI.
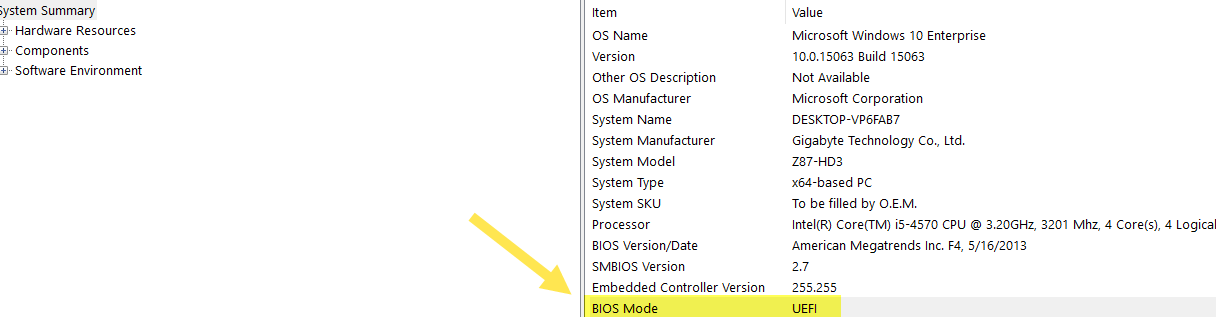
My Bios mode is UEFI:
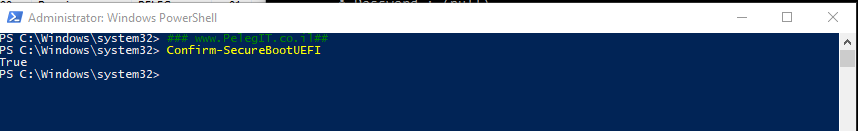
Self-check if UEFI and Secure boot are enabled with Powershell: (Value True means Yes, False No)
Confirm-SecureBootUEFI
After restarting the computer “Credential Guard” began to work:

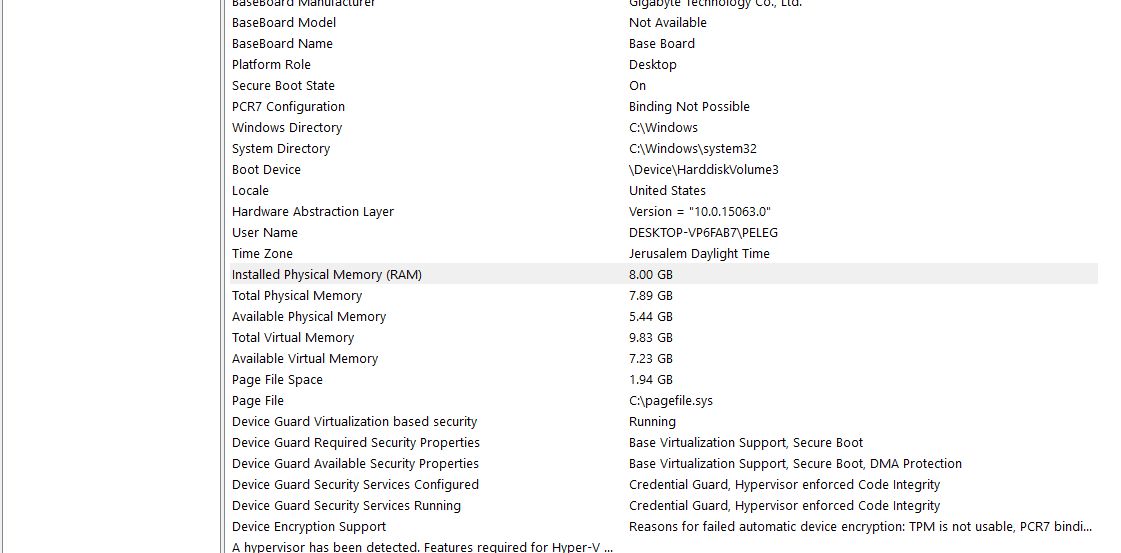
Make sure you have these settings on MSINFO32:
Let’s open the MimiKatz again and rechecking what is going on know after we have enabled the credential guard
Run the following commands:
mimikatz # privilege::debug mimikatz # sekurlsa::logonPasswords full
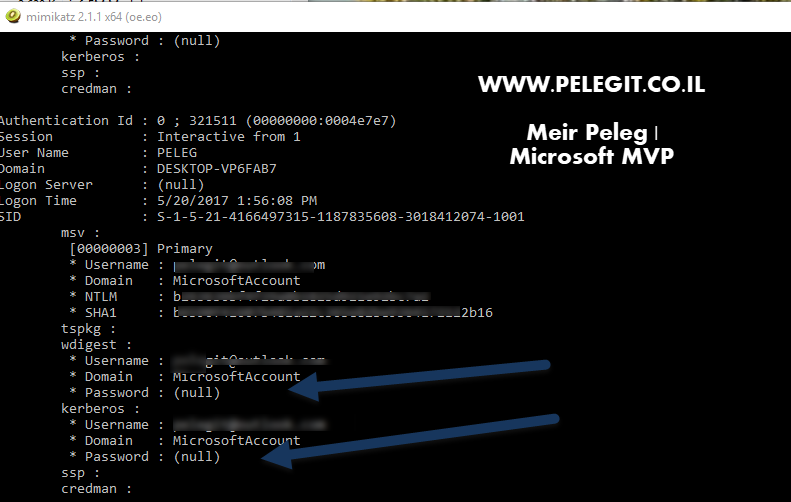
As you can see Password field are (Null) which is comply to our expectation
Great, I hope you have realized what a risk you have under your nose,
And now go to make a coffee and implements this immediately, because meanwhile, your corporate is under risk, today you have the ability to get a report of which computers meet Credential Guard requirements, make use of this reports and plan the project safety- do not wait
Device Guard article is coming up…