Windows Server 2012 Group Managed Service Account
Hello,
In this article, I would like to talk a little bit about “gMSA” and show you how we can seal another hole in our IT environment.
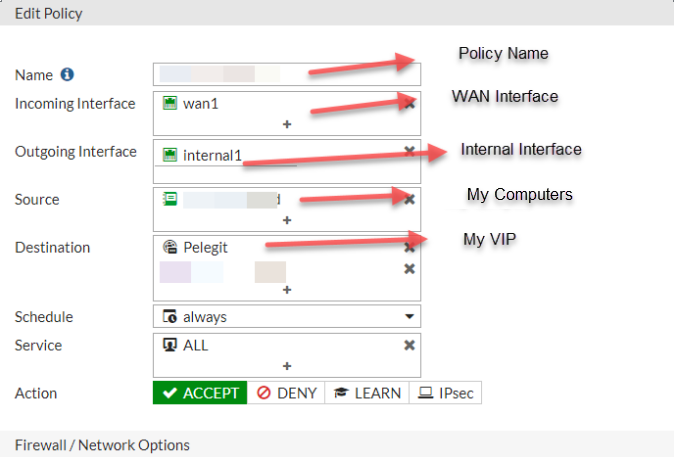
As soon as you’re installing Windows Server 2012 one of the newest features you got is “Group Managed Service Account”, the gMSA comes to help you to manage safety Windows Services and Task schedulers.[IIS] as well.
Before detailed explanation, Active Directory based Windows Server 2012 has a new object class called “gMSAs – msDSGroupManagedServiceAccount” which added in extending schema process automatically.
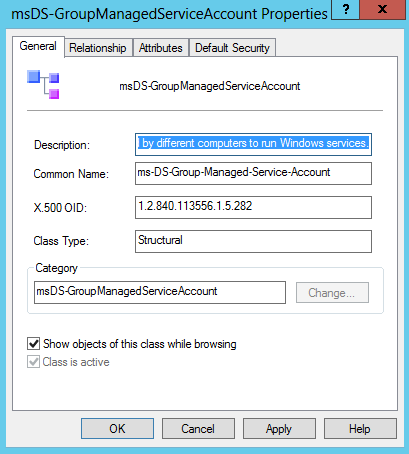
gMSA requires at least Windows Server 2012 Domain Controller, Windows Server 2012 or Windows 8/ Windows 10 for PowerShell module.
While we have to create a task schedule or set a service account to a service we need to set a password which could be exposed whenever & somehow, this is one of the biggest holes on Windows platform.
There are many tools which know to retrieve the password, what happens if you need to run the task with high privilege? in the most cases you put domain admin account and from this point, the penetration possibility increased, can you believe?you have high risk which created by yourself. <System Administraotr>
I bet you 65% out of IT teams using domain admin user for runs their task schedulers, hurrying to finish the task but don’t think about it, because of you see the black point of password…
……….
It doesn’t matter you have complex password policy, anti-virus, or hardening your environment with GPO & third-party tool, you become hacker mate without being aware 🙂
Therefore, I want to show how to make the same purpose in a safe way.
The 1st stage is to add KDSrootkey,
As you know KDS [KEY DISTRIBUTION CENTNER] is responsible for distributing keys and knows to work in collaboration with Kerberos protocol, the KDC gets the request for tickets [TGT].
- How to add KDSrootkey
Open a PowerShell module from your Windows Server 2012 domain controller:
And run the following command:
Add-KdsrootKey

Now you have to wait pretty much 10 hours till all DC’s have replicated and make sure they can respond to gMSA requests.
If you are not a patient one, you can go over the following article and speed up the process:
https://technet.microsoft.com/en-us/library/jj128430.aspx?f=255&MSPPError=-2147217396

The 2nd stage is to go to your domain controller and create a new group of Active Directory Administrative Center:

The 3rd stage is to open PowerShell and run the following command
–Name = you have set the “Service Account” you want to call –DNSHostname “Name of your DC” –PrincipalsAllowedToRetrieveManagedPassword “group name”
New-ADServiceAccount -name <ServiceAccountName> -DNSHostName <fqdn> -PrincipalsAllowedToRetrieveManagedPassword <group>

# Pelegit group is used to manage all hosts we want to manage using gMSA, so don’t forget to add the machines to the group.
A new service object in the AD has been created:

Install-AdServiceAccount <gMSA>
Test-AdServiceAccount <gMSA>
If you are getting the error message “Access Denied” it means you have to add the machine object to the group you have created, and then restart the server.

Good, now you can setup a new task scheduler without inserting password,
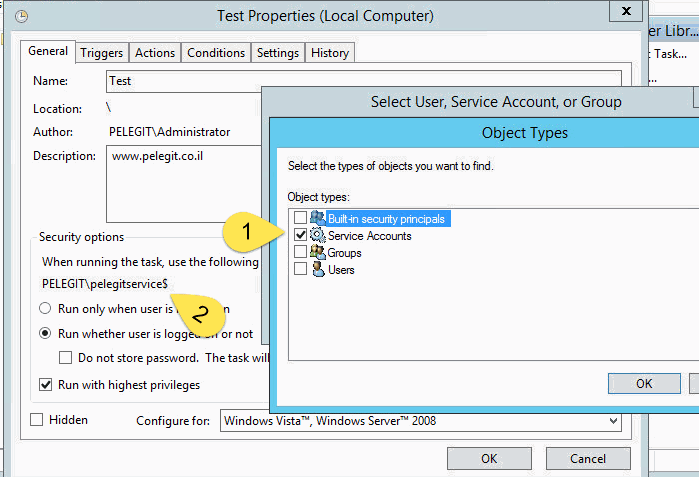
Do not forget to grant you gMSA the ability to run batch job