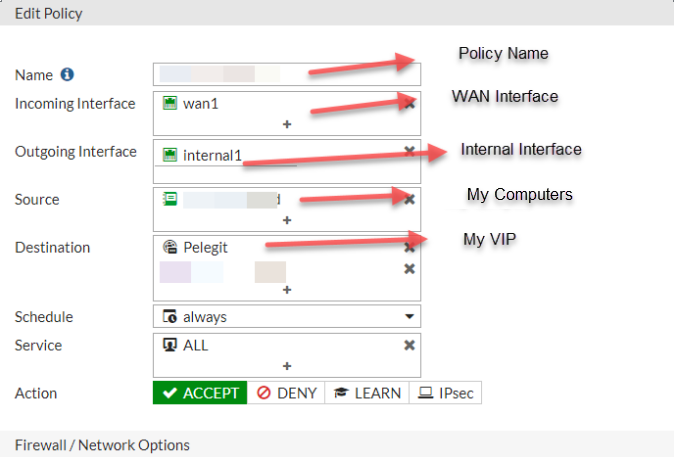
As we all know, many organizations deal with mail attacks on a daily basis. Transport rules have been created & some mail filters are known for protecting against vulnerabilities,
Today I would like to share with you an experience I had with some customers who are not sure how to configure their SPF records correctly to protect against spoofing
What is SPF? acronyms ‘Sender Policy Framework’
A SPF record is actually a DNS record, SPF records contains a list of servers that are allowed to send mails from your domain or who is authorized to send mail from your domain. There are simple thing you can do with your SPF record that can help fight email spam.
SPF consists of the following entries:
Domain.com = the domain the SPF applies to
IN TXT = DNS zone record type
v=spf1 = Utilizing SPF Version 1 and identifies the TXT record as SPF record
a= lists of domain / hosts which allowed to send emails
include = allows to whole domain sends emails, for example (_spf.google.com.) Googles can remove or permitted mail server without you having to change you DNS.#
-all – Hardfail means that don’t accept a mail if the SPF verification failed
~all – Softfail, means even if SPF verification failed you receive emails but the emails marks as
failed
+ all = Lol, allows to any server sending emails from your domain, [ you hadn’t better use in this option]
How does SPF look like?
C:\Users\PELEG>nslookup Default Server: ns-pt-vip.012.net.il Address: 80.179.52.100 > set q=txt > google.com Server: ns-pt-vip.012.net.il Address: 80.179.52.100 Non-authoritative answer: google.com text = "v=spf1 include:_spf.google.com ~all"
How to create SPF?
You can use the following websites, helps you to generate a SPF record
http://www.kitterman.com/spf/validate.html
Let’s talk a little bit about the SPF deeply.
# Telnet alt4.aspmx.l.google.com 25 you get answer from 220 mx.google.com ESMTP 32si17354615plf.34 – gsmtp,
By default, without SPF anyone can send email internally to your domain with your domain for example if my email is [email protected] each one can open TELNET and type Mail From: [email protected] > RCPT TO: [email protected] > data > Subject: SALARY > . > . a mail goes directly to [email protected] , it happens because that I didn’t ask for check SPF record, let’s say I set it for checking SPF, what was happing? here is my SPF
Pelegit.co.il text =
“v=spf1 include:spf.protection.outlook.com -all”
As soon as an external user will try to send Email From: [email protected] > RCPT TO: [email protected] the email reach to PelegIT mail servers and check if the sender is permitted to send mails from @PelegIT.co.il by checking his SOURCE IP (every email has source & destination IP ) the source IP is not one of the IPs allowed to send on behalf PelegIT. The message automatically be rejected because of -all value, if my SPF was set with ~all the messages will be “softfail” which is more lenient {the mail still be accepted with kind of warning on the header) .. Imagine the biggest companies such as Google, Outlook.com, Facebook, don’t have SPF, then everyone could spoof emails from those companies.
BTW – Allowing bad sender on SMG can be the same effect if you do not have any external service that sending external on behalf your domain you just can apply bad sender, but you may maintain the bad senders constantly